Why is it important to have an IT security consultant?
Having an IT security consultant is crucial. This is because all companies must:
- Protect corporate and customer data from threats such as cryptolocker and data theft
- Maintain business continuity by keeping IT systems functioning, efficient, and secure
- Protect workforce and mobile devices, even in BYOD scenarios
What is spam and why you should have it
Spam is a problem that puts your job at risk! Identifying and eliminating spam from your mail means wasting time and reducing productivity. In addition, there is a real possibility that spam messages contain viruses that can infect the entire network and cause much more serious damage to the entire infrastructure. The solution adopted by Simatica is Libra Esva. Awarded and certified “Best antispam since 2012” by Virus Bulletin.
How does Simatica work as an IT security consultant?
Our solution as an IT security consultant is cloud. This means stopping spam before it reaches the company’s mail server, reducing Internet traffic from receiving unnecessary messages. We also use an antispam engine with 13 levels of analysis and 99.96% spam detection. It includes enterprise-class features such as greylisting, Bayesian analysis, header analysis, and body messages. But also filtering on counties, sender policy framework (SPF), recipient verification and more. Of course, you can create custom blacklists for users or domains.
Advantages offered by Simatica
- Advanced Multilevel Antispam Protection
- Up to three Antivirus engines
- Full email tracking with Audit and Delivery Reports
- Smart Newsletter Management
- Phishing and Malware detection
- Ability to filter attachments to emails
- Content filtering to set rules on irrelevant and unwanted content
- Antivirus protection
- Kaspersky Endpoint Security for Business
What is Kaspersky Endpoint Security for Business?
Kaspersky Endpoint Security for Business is the solution adopted by our IT security consultant. It’s an integrated management console that provides centralized control over all Kaspersky Lab endpoint security technologies running in the enterprise environment. Kaspersky also provides a set of pre-configured policies to enable rapid implementation of network security. Small and medium-sized enterprises face many of the same threats that affect large companies. However, management and protection resources are often lacking.
Which next-generation firewall uses Simatica?
Sophos XG Firewall (next generation) is optimized for modern businesses, providing all the protection and analytics features needed in one powerful and easy-to-manage device. Each of these Firewalls comes with basic Firewall functionalities. These include IPSec, SSL VPN and Wireless Protection. You can extend the scope of security action with our Total Protection packages, or even by adding individual security modules.
Other IT security Cnsultant services offered by simatica
As your IT security consultant, we’ll be able to offer you many other services:
Network Protection: stop the most sophisticated attacks and advanced threats
Wireless Protection: setting, managing, and securing Wireless Networks
Web Protection: complete web security and application control features
Security Heartbeat: connect your Sophos endpoints to the firewall, thus protecting against advanced threats
Email Protection: full protection for SMTP and POP messages against spam, phishing, and data loss
Web Server Protection: Enhanced protection for web servers and enterprise applications against hacking attempts
Request an appointment with our IT security consultant
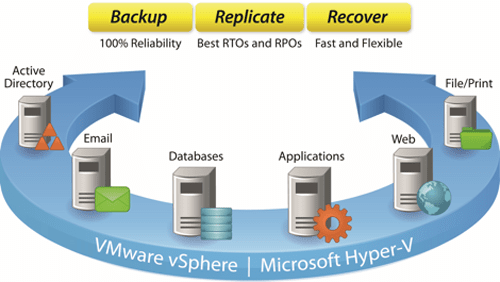
Business Continuity

Backup & Storage

Cloud & Hosting
[/fusion_title]

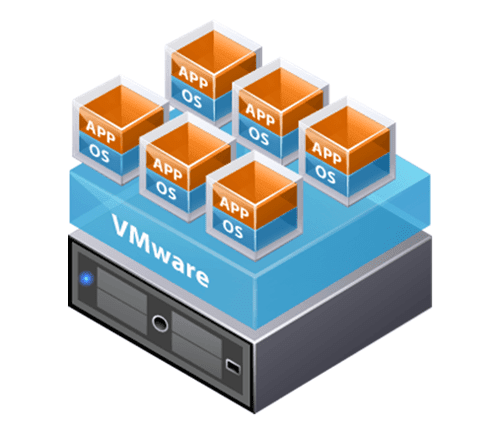
Virtualization
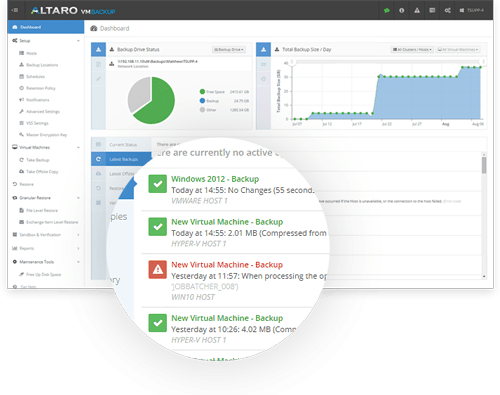
Backup software
ALTARO VW Backup
NAS Storage – Hyperconvergency
QNAP NAS QTS

SYNETO
Cloud & Hosting Services
Thanks to our IT security consultant you can also:
- Register your domain and easily create your own website
- Hosting Linux and Windows
- Enhance your online space with Virtual Servers and Cloud Servers
- Email, SSL Certificates, and PEC Mail
VMWare and Hyper-V Virtualization
Upgrade your switchboard! Cut costs and increase profits! Call from anywhere in the World. Android, iPhone, Mac and Windows.
With 3CX clients for Android and iPhone, you can take your interior wherever you go. 3CX offers the “unique number” concept, meaning you no longer have to give your mobile number around. Set your status so your colleagues can see if you’re available to take a call.